[ad_1]
US Space Force engineer Jason Lowery has urged the Defense Innovation Board to investigate whether a proof-of-work protocol like Bitcoin (BTC) can become of National Strategic Importance.
As Bitcoin hit $41,000 on Monday, theories are circulating that the flagship crypto has the potential to be of strategic significance for cybersecurity.
Jason Lowery Proposes Converting Bitcoin Proof-of-Work to Macrochip
The fundamental concept behind ensuring security across land, sea, air, and space revolves around creating formidable physical barriers to access. One illustrative example of this principle is the construction of forts atop hills, strategically positioned to present a physical challenge to potential adversaries and safeguard against intrusion.
Similarly, Lowery explained that the increased physical barriers can also protect cyberspace. He explained:
“The strategy involves using a physically resource-intensive computer. By designing a computer that is physically costly to operate and making its use mandatory, we can effectively introduce physical constraints into cyberspace and then impose them on anyone operating in, from, and through cyberspace.
“This could be achieved by building and integrating such a computer into the internet infrastructure, thus transposing real-world physical restrictions into a previously unrestricted digital realm for miscellaneous cybersecurity applications.”
Microchips make the computation processes faster. But, for resource-intensive computation, Lowery proposed the idea of “macrochip.” He believes the global electric power grid can be converted into a “massive-scale, energy-intensive, general purpose computer or a macrochip.”
According to Lowery, the macrochip already exists, hiding in plain sight, i.e., Bitcoin’s proof-of-work. He said:
“Proof-of-work technologies, as exemplified by Bitcoin, have the potential to significantly reshape our understanding of warfare in the cyber domain. At the very least, these innovations are already transforming our understanding of cybersecurity.”
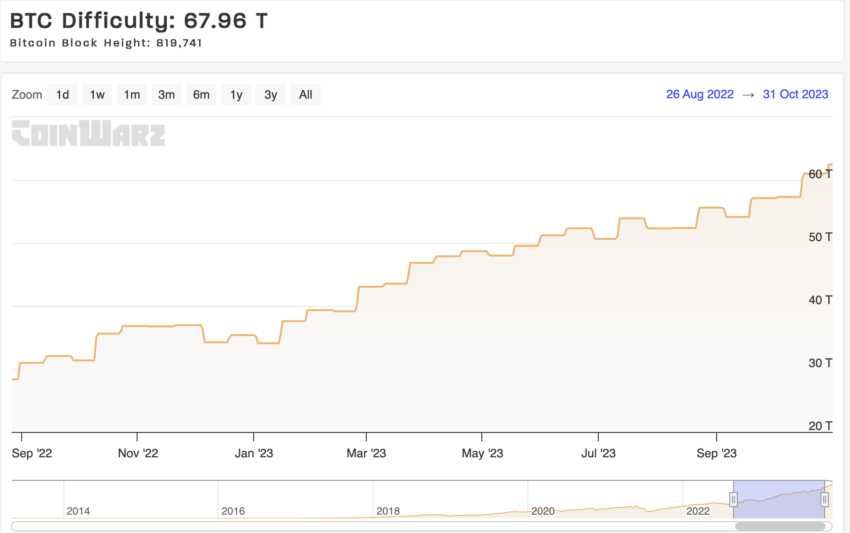
As a matter of fact, Bitcoin’s validation through proof-of-work is an energy-intensive task, requiring huge computation power. As of writing, the Bitcoin difficulty is at 67.96 terahashes per second. The metric measures the difficulty in mining a block of Bitcoin in terahashes.
Read more: Simplifying the Bitcoin White Paper: A Comprehensive Guide
Hence, through a four-page open letter, Lowery recommended the Defense Innovation Board to “prioritize the investigation of the national strategic importance of proof-of-work protocols like Bitcoin.” Previously, in March, through his Massachusetts Institute of Technology (MIT) master’s thesis, he suggested that the US should stockpile Bitcoin as a self-defense weapon.
A Misunderstanding?
Many have contrary opinions against Lowery’s proposal. For instance, John Bethancourt, a retired Air Force officer, believes there is some misunderstanding in Lowery’s idea. He argues:
“PoW is a mechanism for achieving consensus and trust in a distributed ledger by requiring computational work to validate transactions and create new blocks. It does not provide data encryption or secure information from unauthorized access. It is designed to prevent double-spending and ensure the integrity of the blockchain, not to protect data or network infrastructure from cyberattacks.
PoW does not shield data from unauthorized access, exploitation, or theft.”
Read more: How To Buy Bitcoin (BTC) and Everything You Need To Know
Do you have anything to say about Bitcoin proof-of-work or anything else? Write to us or join the discussion on our Telegram channel. You can also catch us on TikTok, Facebook, or X (Twitter).
For BeInCrypto’s latest Bitcoin (BTC) analysis, click here.
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content.
[ad_2]
Source link