Table of Contents
A Single Mistake Led to a $50M Loss
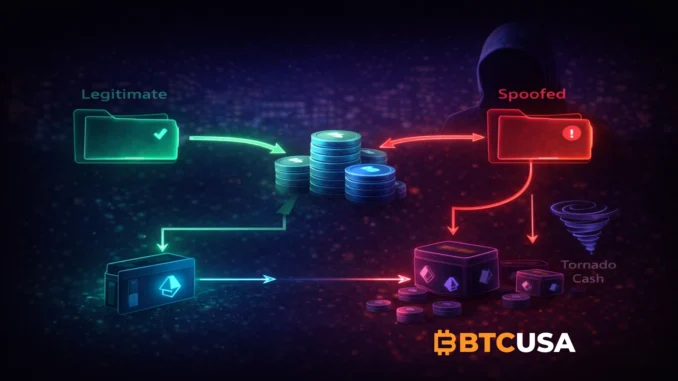
According to SlowMist monitoring, a cryptocurrency user has lost nearly $50 million in USDT after falling victim to an address-poisoning scam — a technique that exploits transaction history rather than smart contract vulnerabilities.
How the Address Poisoning Scam Unfolded
The incident occurred when the victim copied a wallet address directly from their transaction history, believing it belonged to a trusted recipient. Unknown to the user, an attacker had previously sent a small transaction from a look-alike address designed to closely resemble the legitimate one. As a result, the victim mistakenly transferred 49,999,950 USDT to the attacker’s wallet.
Address poisoning scams rely on subtle visual similarities between addresses and exploit common user behavior, making them particularly dangerous even for experienced participants.
Rapid Laundering via Ethereum and Tornado Cash
Following the transfer, the stolen USDT was quickly converted into ETH. The attacker then split the funds across multiple wallets — a standard obfuscation technique — before moving part of the ETH into Tornado Cash in an apparent attempt to break on-chain traceability.
The speed and structure of the laundering process suggest a highly prepared operation rather than an opportunistic attack.
Victim Issues On-Chain Ultimatum
According to Specter, the wallet associated with the loss later posted an on-chain message directed at the attacker. In the message, the victim demanded the return of 98% of the stolen funds within 48 hours to a specified address.
The message proposed allowing the attacker to retain approximately $1 million as a so-called white-hat bounty in exchange for cooperation. It further warned that failure to comply would result in escalation through legal channels, including engagement with international law enforcement and pursuit of both criminal and civil action.
A Growing Threat to Self-Custody Users
Address poisoning attacks have become increasingly prevalent as on-chain activity grows. Unlike phishing websites or malicious smart contracts, these scams exploit wallet UX limitations and human error, leaving victims with little recourse once funds are transferred.
Security researchers continue to warn that copying addresses from transaction history without full verification remains one of the most common causes of large-scale crypto losses.
BTCUSA Insight
This incident underscores a critical weakness in crypto self-custody: the reliance on visual address recognition and transaction history shortcuts. Address poisoning does not exploit smart contracts or protocols, but human behavior and wallet UX design. As on-chain volumes grow and transfers reach institutional scale, these subtle attack vectors pose outsized risks. While post-incident negotiations and legal escalation may sometimes lead to partial recovery, they are not a security model. The long-term solution lies in stricter address verification, whitelisting, and wallet-level safeguards that treat every transfer as irreversible by default.


